
 |
|
|||||||
| 論壇說明 |
|
歡迎您來到『史萊姆論壇』 ^___^ 您目前正以訪客的身份瀏覽本論壇,訪客所擁有的權限將受到限制,您可以瀏覽本論壇大部份的版區與文章,但您將無法參與任何討論或是使用私人訊息與其他會員交流。若您希望擁有完整的使用權限,請註冊成為我們的一份子,註冊的程序十分簡單、快速,而且最重要的是--註冊是完全免費的! 請點擊這裡:『註冊成為我們的一份子!』 |
|
|
主題工具 | 顯示模式 |
|
|
#1 |
|
榮譽會員
 |
Jetico in ubuntu Way 之:去蕪存菁
主題:Jetico in ubuntu Way 之:去蕪存菁 (無廢話帶你解讀JPF手冊的精華部分,及我在使用中的經驗) 作者:ubuntu 版權聲明:本文采用創作共用協議 在遵守創作共用協議,非商用,非盈利以及保留作者和版權聲明的前提下,您可以任意轉載本文。將本文用於商業用途請先聯繫作者,以獲得授權。作者不對讀者使用本文中軟件造成的損失承擔任何責任。 本文作者保留對違反本聲明的行為進行法律訴訟的權利。 附加聲明:在互相尊重的前提下,歡迎任何人指正及討論,本人願意回答與本帖有關的問題。與本帖無關問題,概不回答。您可以開新帖詢問其它有關Jetico的問題。對於不調查,不舉證,一概憑主觀臆測的評論,本人一律不予回復,以免口舌之爭。本人誓死捍衛您的言論自由,但前提是您要拿出令人信服的證據。 本來不打算再寫這種吃力不討好的指南,但是看到論壇有的朋友PM詢問一些問題,我決定寫完,回報給支持我的人。 工欲善其事,必先利其器。要想用好JPF必須通讀幫助手冊。由於手冊是英文的,好多人不願意看,我就把精華部分挑出來,並結合自己的使用經驗,寫成此文。 說句實話,Jetico的手冊又臭又長,很多問題可以有更好的表達方式,它不用,我也懶的看。不過整個手冊,我還是看過的。 要設置規則,就得講原理,就要看手冊。知道英文的手冊有人懶的看,下面我揀最重要的講。詳細去看手冊,不多解釋。 JPF手冊英文的,裡面廢話一大堆。當然也有有用的。 下面我寫的,就是精華部分,你看不懂的話,就不要折騰啦,安全第一。我不管它JPF怎麼設計的,底層怎麼過濾的,它是三層也好,或者和樂百氏搞個幾十層。我只要事件,規則。 問題1:Root Table;Root Table由Application Table,Process Attack Table,Protocols Table,System IP Table,reject組成,不用看Jetico,你能記得它們的順序嘛? 問題2: 下面兩種情況,你會如何選擇? 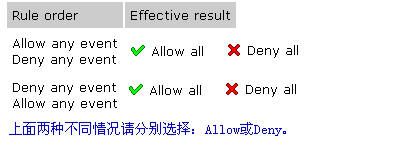 JPF管規則叫Rule,以後俺也叫Rule。 Filter,Event,Rule,再折騰也離不開這三個。牢記。 Rules of different types control different events. 牢記。 JPF的三層filter Network Packet filter (由IP filter和Protocol filter組成) Application filter Process attack filter 看下面兩張圖,很好理解。TDI Filter就是Application Filter,它是內核級網路驅動的最高層,直接面向用戶級應用。 由於Network filter有兩部分,所以有4個過濾模塊。 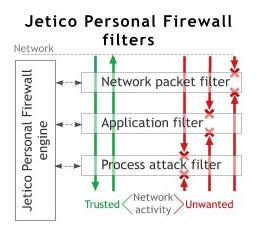  Filter,Event,Rule三者的關係 Network packet filter 對應的 Rule types: Network protocol rule IP rule Application filter 對應的 Rule types: Application rule Process attack filter 對應的 Rule types: Process attack rule 去JPF -> configuration -> Optimal Protection -> Root 看到了嘛? 四種Rules對應於4個Table,實際上是4個規則組,Table就是規則的容器。 都用過Windows,Table就像資料夾,規則就像資料夾裡的文件。複雜嘛? 一點都不複雜。 QUOTE: Network packet filter 對應的 Rule types:Network protocol rule; IP rule Network protocol rule 對應的Events: Event - select whether to match incoming packets, or outgoing packets or both IP rule 對應的Event Event - select whether to match incoming packets, or outgoing packets or both QUOTE: Application filter 對應的 Rule types:Application rule Application rule,對應的Events: Event - application network event type: any inbound connection outbound connection listening port receive datagrams send datagrams listening datagrams access to network any - any event is suitable inbound connection - connection with local application initiated by remote end outbound connection - connection to remote server initiated by local application listening port - local application waits for incoming connections receive datagrams - local application receives data within connectionless communications send datagrams - local application sends data within connectionless communications listening datagrams - local application waits for incoming data within connectionless communications access to network - special event which means general access to networking subsystem preceding to all network communications. While 'access to network' is not enabled for an application, it won't be permitted to execute any network-related function QUOTE: Process attack filter 對應的 Rule types:Process attack rule Process attack rule,對應的Events: attacker installs system-wide Windows hook Attacker starts application with hidden window Attacker writes to application's memory Attacker injects own code into application Attacker modifies child process Low-level access to system memory Attack type - suspicious action type attacker installs system-wide Windows hook Microsoft Windows operating systems provide so-called hooking mechanism. Application are allowed to install 'hook' function which can intercept some events (mouse actions, keystrokes, etc.) before they reach the target application. The key point of some hooks is that hook function code must be executed on behalf of other application. Windows hooking mechanism is widely used both by legal applications and trojans. As soon as trojan installs Windows hook, it can access network via its hook function. Since the hook function can reside in legal process' space (for example, in Explorer.exe process), the user will not realize that network is accessed by the trojan. Attacker starts application with hidden window Trojan program can run another trusted application with command-line arguments and make the application accessing network. Of course, the user will notice that something is going wrong if he/she sees unexpectedly appeared Internet Explorer's windows. So the trojan program can simply run Internet Explorer's windows in hidden mode. Jetico Personal Firewall reports about the event, but it should be noted that legal programs often run their modules with hidden windows, for example, when such a module supports icon in the system tray. Attacker writes to application's memory. Trojan program can modify memory of another trusted application. Usually trojan replaces contents of memory where legal code of the trusted application resides by the code of the trojan's procedure that accesses network. As soon as the procedure runs, it accesses network so that everything looks like the trusted application itself decides to access network. Attacker injects own code into application. When Windows application runs, it may have one or several so-called "threads". Every thread works in parallel with other threads and executes its own code in the context of the application's process. Windows allows creating of remote threads, i.e. one process can create thread that will work in context of another trusted process. In this case Windows beleives that this trusted process is responsible for everything that the remote thread makes. Trojan programs can use the technology of remote threads to hide their activity. Attacker modifies child process. Trojan program (attacker) can run another trusted application and modify its memory before the process of trusted application will run. Since the trusted process is not running yet, it may be difficult to detect after some time that the trusted application will run the code of trojan program. Low-level access to system memory. Trojan program can harm loaded Windows system modules or running applications by modifying contents of system physical memory. Since the physical memory is common for all the processes running on the computer, such a dangerous program can make any process doing what the trojan program wants. Windows security mechanisms normally does not allow programs to make such a trick, but it is still possible. If Jetico Personal Firewall detects this kind of attack, it definitely means that the reported program is a trojan. 看明白沒,三大filter,都是處理各自的Events,沒有交集。他們是平行關係,不是從屬關係。那麼filter是做什麼的? 1.攔截屬於自己的Event,然後2. 去Security Policy裡,通常是Optimal Protection裡查找對應的Rules,根據Rules對Events進行處理。 Allow or Block 這就是問題所在。 Root Table;Root Table由Application Table,System IP Table,Protocols Table,Process Attack Table,reject組成。Root Table是個特例,只有它包括任何類型的規則,可以處理任何類型的事件。其它Table只能接受特定的事件和規則如:Application Table只能處理Application Event,而不能處理Process Attack Event。 Rules of different types control different events. 牢記。 意思就是說,不同的Rule支配管理駕馭對應不同的Event。再詳細點:比如,svchost.exe inbound connection TCP local 135 port Event發生了,事件只會在Application Rule Table裡找到匹配的規則,它絕不會在IP Rule Table裡找到匹配的規則。不屬於這個Event的Rule全部被無視了,它們相當於不存在。 於是,我看到有人問,都是屏蔽135連接阜的Rules,到底是svchost.exe裡的優先,還是IP Rules裡的優先。 我現在告訴你,它們是平行的,沒有優先級的關係。JPF只會根據Events來選擇對應的Rules。如果事件屬於Application Table,Application rule被執行,無視System IP Table。如果事件屬於System IP Table, System IP rule被執行,無視Application Table。 處理問題要抓主要矛盾,你看看Process attack filter的介紹太煩了,我們先把Process attack filter忽略掉。為什麼,比如JPF有很多視窗是由Process attack filter彈出的,實際沒聯網你就開始彈視窗啦,我不喜歡這個,我只要它在聯網的時候才彈出視窗,這點做的沒CPF好。有人說關了不安全,那好,既然是不聯網你都彈,我關掉你,裝PG或 SSM GSS或者KAV6的Proactive Defence,這樣即減少了JPF的複雜性,又不損失安全性,兩全啊。注意Process attack filter不監控網路訪問,關掉Process attack filter,並不影響其它filter對網路訪問的監控,這需要你瞭解Process attack filter對應的事件。 Network protocol rule,IP rule 這兩個沒點基礎的人,也不會設置,先丟一邊,以後再說。 那麼我們的重點就是Aplication Rules,實際上就是Application Rules裡的Ask User,就是這裡。 Application Rule搞定後,再去設置Network protocol rule,IP rule 最後你有興趣的話再去設置Process attack rule。 規則的匹配是自上到下的順序,這點要記住。 所有Action的圖示說明: 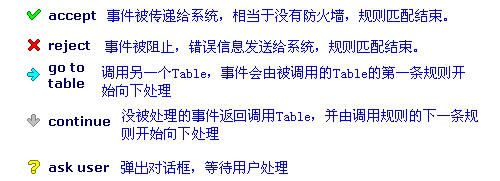 Application Rules相關事件Event的說明: 我說JPF的手冊廢話一大堆,可不是胡說。比如下面這些事件: QUOTE: Event - application network event type: any inbound connection outbound connection listening port receive datagrams send datagrams listening datagrams access to network 然後你去看手冊對事件的解釋,一般人根本不知道它在說什麼。 你按字面直譯:向外連接,向內連接,接收資料,發送資料,監聽連接阜,監聽資料,訪問網路? 翻譯完了,天書嘛!你也搞不清它在說什麼?你Event都搞不清楚,寫出來的規則還不是一塌糊塗。 我下面用Rule Based Firewall的語言來解釋一下,真正給防火牆寫過規則的人,應該能看明白。我知道給OP,Kerio寫過規則的人看者比較親切。LNS的規則寫法比較特別,熟悉的應該也能看懂。 QUOTE: inbound connection(Jetico) 是 TCP inbound/incoming TCP入站/傳入(OP Kerio Comodo) 在LNS裡要設成TCP雙向(LNS) outbound connection (Jetico) 是 TCP outbound/outgoing TCP出站/傳出(OP Kerio Comodo) 在LNS裡要設成TCP雙向(LNS) listening port (Jetico) 是 listening TCP port 監聽TCP連接阜 receive datagrams (Jetico) 是 UDP inbound/incoming UDP入站/傳入 (OP Kerio Comodo LNS) send datagrams (Jetico) 是 UDP outbound/outgoing UDP出站/傳出 (OP Kerio Comodo LNS) listening datagrams (Jetico) 是 listening UDP port 監聽UDP連接阜 access to network 這個以後再解釋 @@ 很明顯,我的解釋簡單明瞭,手冊裡的說法晦澀難懂。 以上都是我所理解的Jetico手冊裡的精華部分,當然還有一些手冊裡沒有,我自己的觀點。但願它們是有用的。授人以魚不如授人以漁。 QUOTE: 問題: 怎麼設置可以允許一個信任的程式去hook其它的程式?不要讓他總是提示xxxx入侵xxxx的記憶體~~ 答案: QUOTE: add to application trust zone 這是某人問過的問題? 看懂本文的人應該很清楚答案是否正確。 QUOTE: 20060603 第一版發佈 |
__________________
|
|
|
|
送花文章: 3,
|