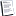
Win 2000下的行程枚舉
行程在每個系統中實現的方法是不一樣的,在 win 98 中,系統提供 TOOLHELP32 API 接頭,在 win NT 中,系統提供 PSAPI 函數, 2000而 win 2000 既支持 TOOLHELP 又支持 PSAPI,NT 系統還提供了 NATIVE API (NtQuerySystemInformation),這個函數功能十分強大,幾乎可以查詢所有的系統資訊,使用此函數必須有SE_TCB_NAME特權。下面給出函數原型:
NTSTATUS
WINAPI
NtQuerySystemInformation(
int SystemInfoClass
PVOID SystemInfoBuffer,
ULONG SystemInfoBufferSize,
PULONG BytesReturned
);
當 SystemInfoClass 等於5時便可獲取行程資訊了。
關於 NT 系統下的特權(Privilege)及其描述見下表:
Privilege Constant Description
SE_ASSIGNPRIMARYTOKEN_NAME Required to assign the primary token of a process.
SE_AUDIT_NAME Required to generate audit-log entries. Give this privilege to secure servers.
SE_BACKUP_NAME Required to perform backup operations.
SE_CHANGE_NOTIFY_NAME Required to receive notifications of changes to files or directories. This privilege also causes the system to skip all traversal access checks. It is enabled by default for all users.
SE_CREATE_PAGEFILE_NAME Required to create a paging file.
SE_CREATE_PERMANENT_NAME Required to create a permanent object.
SE_CREATE_TOKEN_NAME Required to create a primary token.
SE_DEBUG_NAME Required to debug a process.
SE_INC_BASE_PRIORITY_NAME Required to increase the base priority of a process.
SE_INCREASE_QUOTA_NAME Required to increase the quota assigned to a process.
SE_LOAD_DRIVER_NAME Required to load or unload a device driver.
SE_LOCK_MEMORY_NAME Required to lock physical pages in memory.
SE_PROF_SINGLE_PROCESS_NAME Required to gather profiling information for a single process.
SE_REMOTE_SHUTDOWN_NAME Required to shut down a system using a network request.
SE_RESTORE_NAME Required to perform restore operations. This privilege enables you to set any valid user or group SID as the owner of an object.
SE_SECURITY_NAME Required to perform a number of security-related functions, such as controlling and viewing audit messages. This privilege identifies its holder as a security operator.
SE_SHUTDOWN_NAME Required to shut down a local system.
SE_SYSTEM_ENVIRONMENT_NAME Required to modify the nonvolatile RAM of systems that use this type of memory to store configuration information.
SE_SYSTEM_PROFILE_NAME Required to gather profiling information for the entire system.
SE_SYSTEMTIME_NAME Required to modify the system time.
SE_TAKE_OWNERSHIP_NAME Required to take ownership of an object without being granted discretionary access. This privilege allows the owner value to be set only to those values that the holder may legitimately assign as the owner of an object.
SE_TCB_NAME This privilege identifies its holder as part of the trusted computer base. Some trusted protected subsystems are granted this privilege. This privilege is required to call the LogonUser function.
SE_UNSOLICITED_INPUT_NAME Required to read unsolicited input from a terminal device.
SE_MACHINE_ACCOUNT_NAME Required to create a machine account.
於定義可見下表,或察看 WINNT.H:
SE_CREATE_TOKEN_NAME SeCreateTokenPrivilege
SE_ASSIGNPRIMARYTOKEN_NAME SeAssignPrimaryTokenPrivilege
SE_LOCK_MEMORY_NAME SeLockMemoryPrivilege
SE_INCREASE_QUOTA_NAME SeIncreaseQuotaPrivilege
SE_UNSOLICITED_INPUT_NAME SeUnsolicitedInputPrivilege
SE_MACHINE_ACCOUNT_NAME SeMachineAccountPrivilege
SE_TCB_NAME SeTcbPrivilege
SE_SECURITY_NAME SeSecurityPrivilege
SE_TAKE_OWNERSHIP_NAME SeTakeOwnershipPrivilege
SE_LOAD_DRIVER_NAME SeLoadDriverPrivilege
SE_SYSTEM_PROFILE_NAME SeSystemProfilePrivilege
SE_SYSTEMTIME_NAME SeSystemtimePrivilege
SE_PROF_SINGLE_PROCESS_NAME SeProfileSingleProcessPrivilege
SE_INC_BASE_PRIORITY_NAME SeIncreaseBasePriorityPrivilege
SE_CREATE_PAGEFILE_NAME SeCreatePagefilePrivilege
SE_CREATE_PERMANENT_NAME SeCreatePermanentPrivilege
SE_BACKUP_NAME SeBackupPrivilege
SE_RESTORE_NAME SeRestorePrivilege
SE_SHUTDOWN_NAME SeShutdownPrivilege
SE_DEBUG_NAME SeDebugPrivilege
SE_AUDIT_NAME SeAuditPrivilege
SE_SYSTEM_ENVIRONMENT_NAME SeSystemEnvironmentPrivilege
SE_CHANGE_NOTIFY_NAME SeChangeNotifyPrivilege
SE_REMOTE_SHUTDOWN_NAME SeRemoteShutdownPrivilege
ADMINISTRATOR 被預設授於以下這16個權限:
SeChangeNotifyPrivilege
SeSecurityPrivilege
SeBackupPrivilege
SeRestorePrivilege
SeSystemtimePrivilege
SeShutdownPrivilege
SeRemoteShutdownPrivilege
SeTakeOwnershipPrivilege
SeDebugPrivilege
SeSystemEnvironmentPrivilege
SeSystemProfilePrivilege
SeProfileSingleProcessPrivilege
SeIncreaseBasePriorityPrivilege
SeLoadDriverPrivilege
SeCreatePagefilePrivilege
SeIncreaseQuotaPrivilege
可以用 OpenProcessToken 和 AdjustTokenPrivileges 這兩個函數來提升行程的特權。
講了那麼多,現在回到主旨上來。到底使用哪個方法比較好呢?在 win 2000 下有3個方法可供選項,我比較喜歡簡單的方法。NtQuerySystemInformation 功能固然強大,但使用比較麻煩。而 win 2000 的 TOOLHELP32 API 其本質還是使用了 NtQuerySystemInformation 函數,由於它發生錯誤時,可能不能正確返回返回值,所以不是很穩定,使用起來也是很麻煩的,不符合我的懶人本性。還是採用 PSAPI 比較好,簡單又方便,只需要三個函數,且沒有複雜的結構體參數。
函數原型:
BOOL
WINAPI
EnumProcesses(
DWORD * lpidProcess,//游標指向存放行程ID的陣列
DWORD cb, //陣列大小
DWORD * cbNeeded //返回的實際大小
);
BOOL
WINAPI
EnumProcessModules(
HANDLE hProcess, //行程句柄
HMODULE *lphModule, //游標指向存放模組句柄的陣列
DWORD cb, //陣列大小
LPDWORD lpcbNeeded //返回的實際大小
);
DWORD
WINAPI
GetModuleFileNameEx(
HANDLE hProcess, //行程句柄
HMODULE hModule, //模組句柄
LPSTR lpFilename, //存放模組檔案名的字串串
DWORD nSize //字串串大小
);
他們的作用分別是:枚舉行程,枚舉行程模組,獲取模組檔案名(包含路徑)。詳細的來源碼如下:
// EnumProcess.cpp : Defines the entry point for the console application.
// Code By : tabris17
#include "stdafx.h"
#include "Psapi.h"
#pragma comment (lib,"Psapi.lib")
void PrintFileName(DWORD processID)
{
char fn[MAX_PATH];
HANDLE hProcess=OpenProcess(PROCESS_QUERY_INFORMATION|PROCESS_VM_READ,FALSE,processID);
if (hProcess)
{
HMODULE hMod[1024];
DWORD cbNeeded,size;
unsigned int i;
if (EnumProcessModules(hProcess,hMod,sizeof(hMod),&cbNeeded))
{
size=cbNeeded/sizeof(HMODULE);
GetModuleFileNameEx(hProcess,hMod[0],fn,sizeof(fn));
printf("\n(%u)\t%s\n",processID,fn);
for(i=1;i<size;i++)
{
GetModuleFileNameEx(hProcess,hMod[i],fn,sizeof(fn));
printf("\t%s\n",fn);
}
}
}
CloseHandle(hProcess);
}
int plist()
{
DWORD Processesid[1024], cbNeeded,size;
unsigned int i;
if (!EnumProcesses(Processesid,sizeof(Processesid),&cbNeeded))
return 0;
size=cbNeeded/sizeof(DWORD);
for (i=0;i<size;i++)
PrintFileName(Processesid[i]);
return 0;
}
int main(int argc, char* argv[])
{
plist();
return 0;
}
|